Collect data
To collect data you need a tool called SharpHound.exe
Download it from: https://github.com/BloodHoundAD/BloodHound/tree/master/Ingestors
Run the following command with a normal “Domain User” to enumerate Group Membership, Trusts, ACLs, ObjectProps, Containers, and GPO Local Admins within a Domain:
SharpHound.exe -c DCOnly
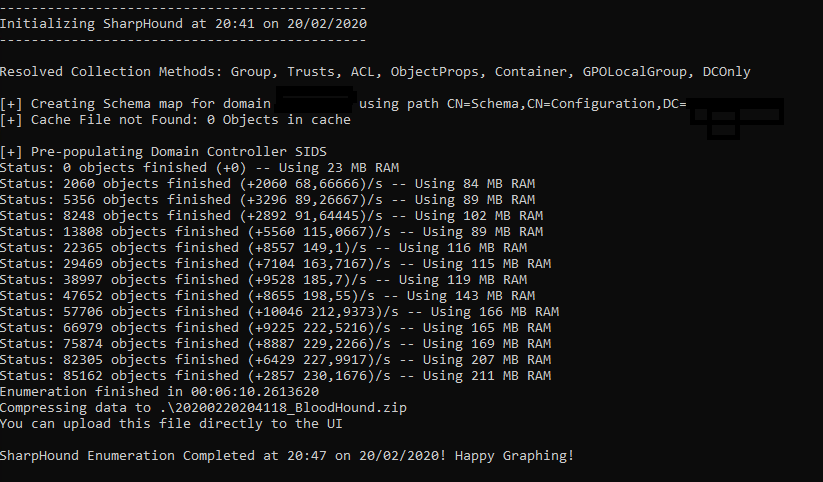
When finished, a zip file should have been generated – example: 20200220204118_BloodHound.zip
Database
Data must be stored in a database. BloodHound is using Neo4J.
Download it from: https://neo4j.com/download/
Make sure to safe your Desktop Key. You’ll need it later.
Install the application and run it (enter your Desktop Key) and Neo4j Desktop windows appears.
Change the Project Name to BloodHound:
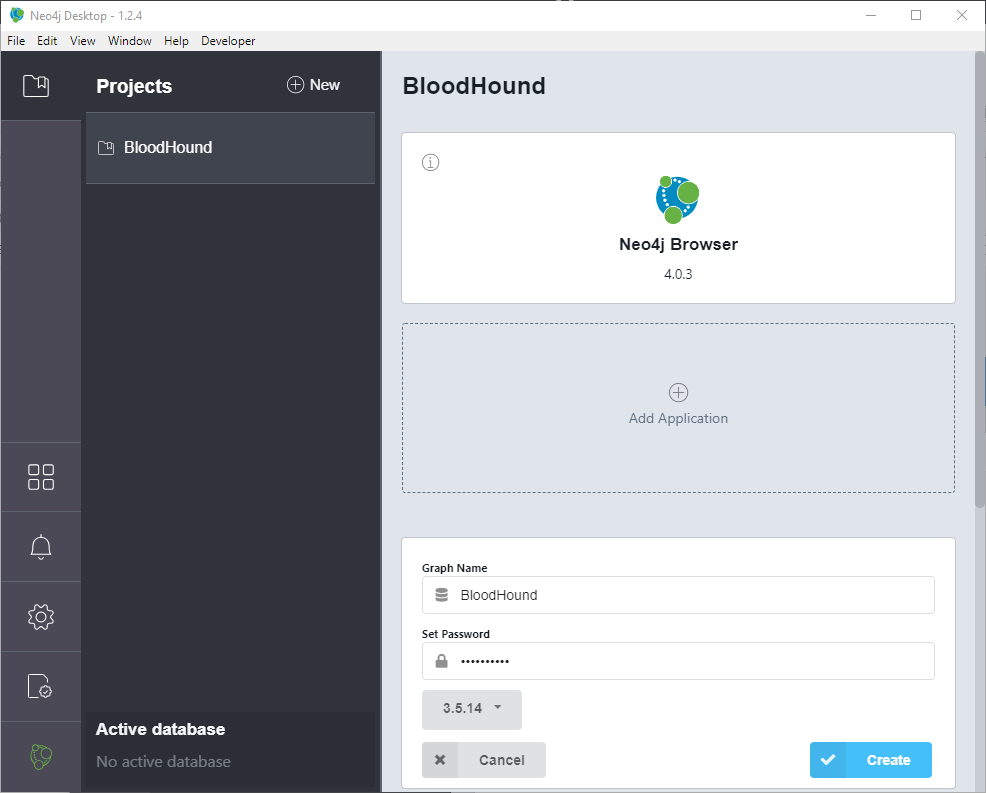
Add a graph: Name it BloodHound and choose a password (need this to login with BloodHound.exe later on) > click Create
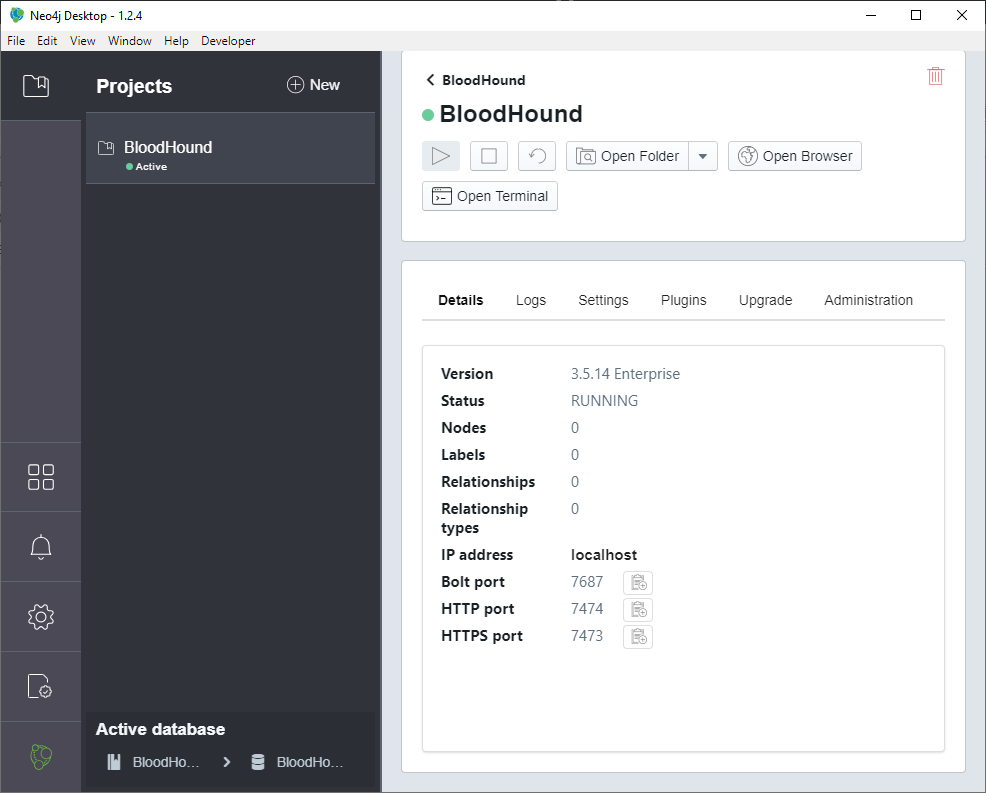
Open the settings of graph BloodHound and start it: Press play button
Visualize data
To visualize the collected data you need BloodHound.
Download it from: https://github.com/BloodHoundAD/BloodHound/releases
Extract the zip file to “C:\Tools\BloodHound”
Start “BloodHound.exe” and enter the password which you’ve set while creating the graph (do not change Database URL and Username!): click on Login
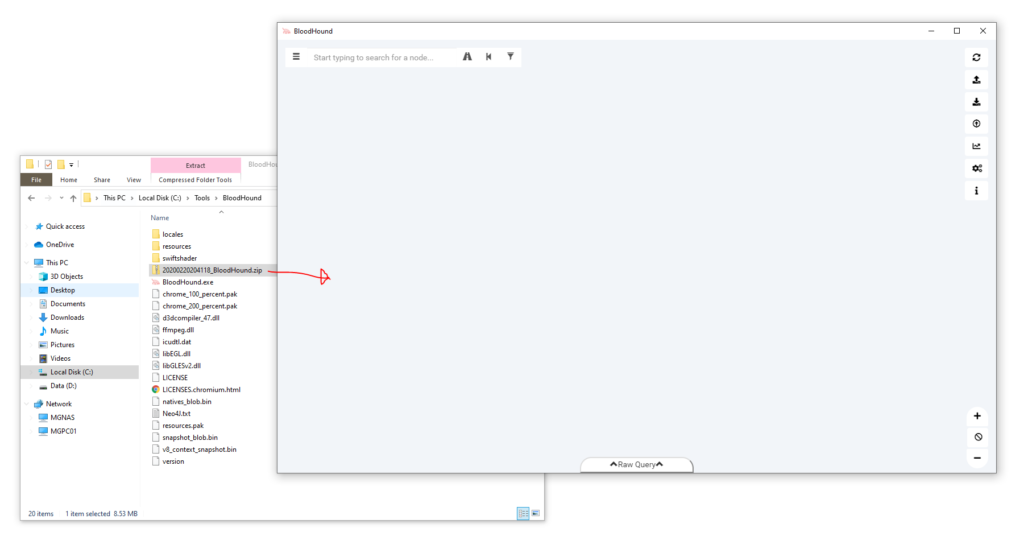
Drag the zip file into BloodHound windows and wait until it’s fully loaded into the database.
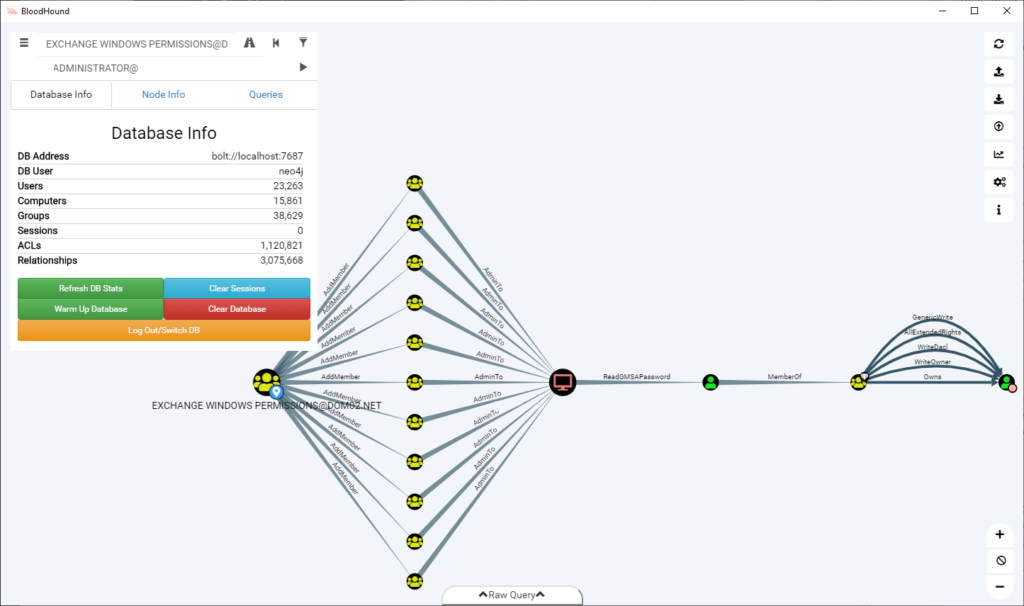
Finding the shortest path to a specific user
Enter the Start Node (user), Target Node (for example Domain Admins) and press Play:

The result will show the path to Domain Admins:
Pre-Built Queries
BloodHound has as well a lot of interesting pre-built queries:

