If you want to run a quick vulnerability assessment on a single Windows system, read the following article.
OpenScap
Update November 2022: OpenScap will not get any further updates for Windows – Therefore, please use the SCAP Compliance Checker (scroll down)
openscap/windows.md at maint-1.3 · OpenSCAP/openscap · GitHub
One of the applications I use is the command line tool OpenSCAP – for Windows client and server operating systems, download the latest msi installer from: https://github.com/OpenSCAP/openscap/releases
Run the setup and open “Windows Explorer” to go to the path where OpenScap has been installed: “C:\Program Files (x86)\OpenSCAP 1.3.4”
Optional: To make sure you do not have to install the executables on every single system, you can just copy the folder to a central location to reuse it later again on other systems.
SCAP content
To compare your system against the STIG (Security Technical Implementation Guides) standard, you have to download the STIG Benchmark file for your operating system.
Go to: https://public.cyber.mil/stigs/scap/
…and download the compressed file:
Copy the extracted XML file to the OpenScap directory:
Run the assessment
Open a “command pompt” as Administrator – change the directory to the OpenScap path and run the following command (use your downloaded XML file in the command!):
oscap xccdf eval –report report.html U_MS_Windows_10_V2R1_STIG_SCAP_1-2_Benchmark.xml
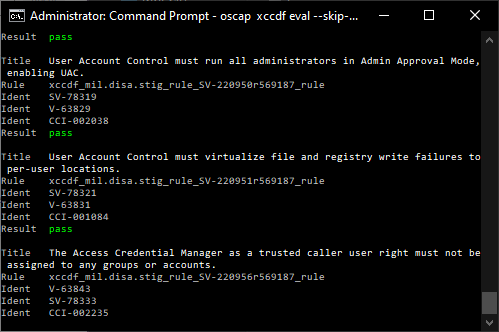
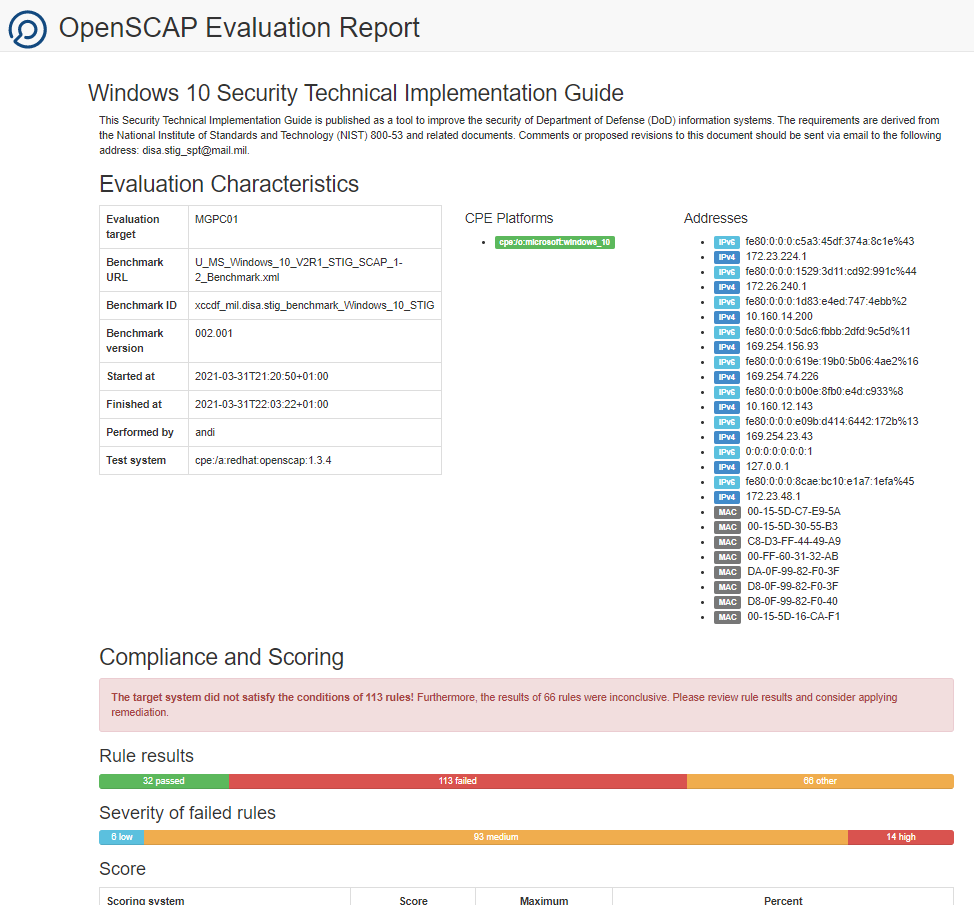
Open the HTML report “report.html” and check each finding and remediate it if possible (depends on compatibility to other systems / system landscape / specific requirements / down Level compatibility / etc.)
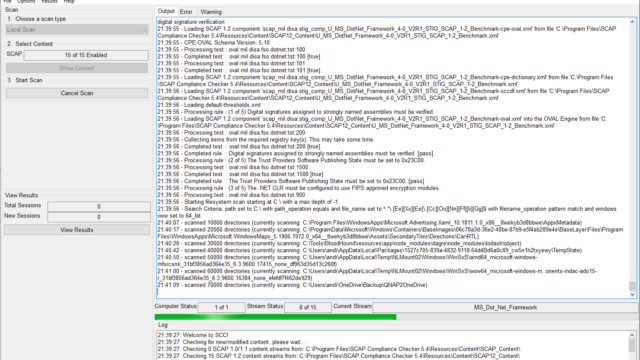
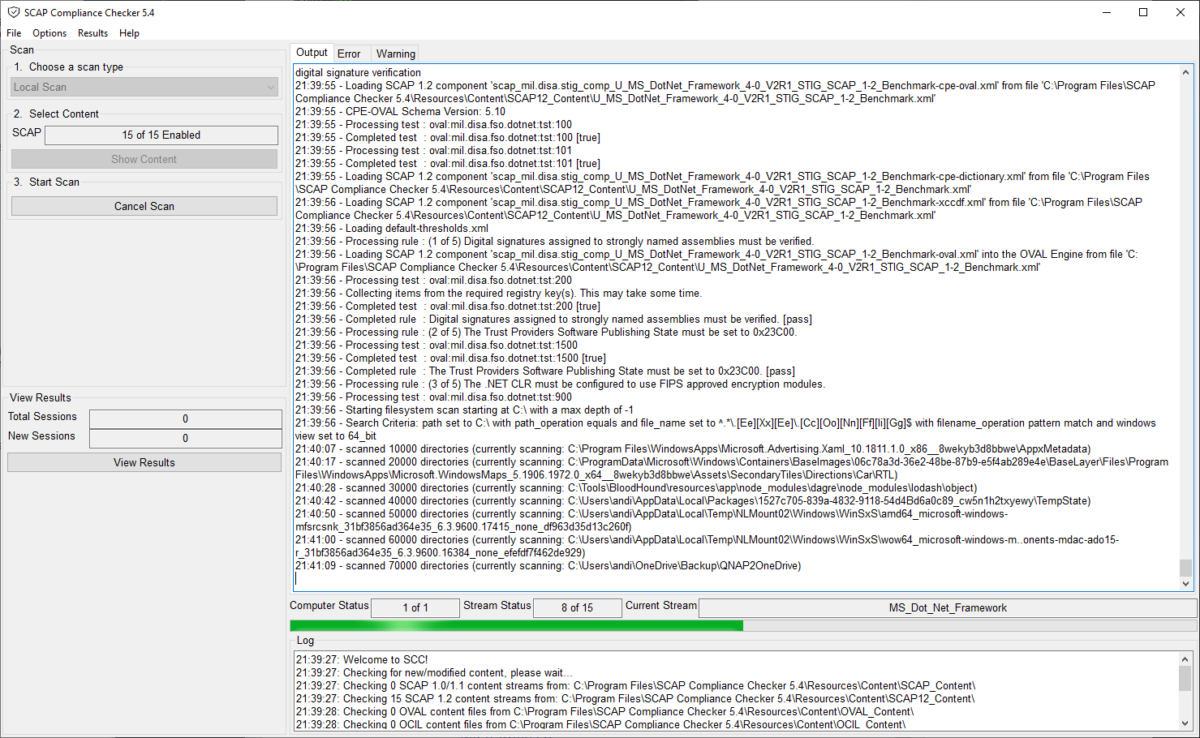
SCAP Compliance Checker (fast & easy)
Another option is the SCAP Compliance Checker – Download “SCC 5.5 Windows” from: https://public.cyber.mil/stigs/scap/
Install the setup and run a scan (by default it checks against all available benchmarks):
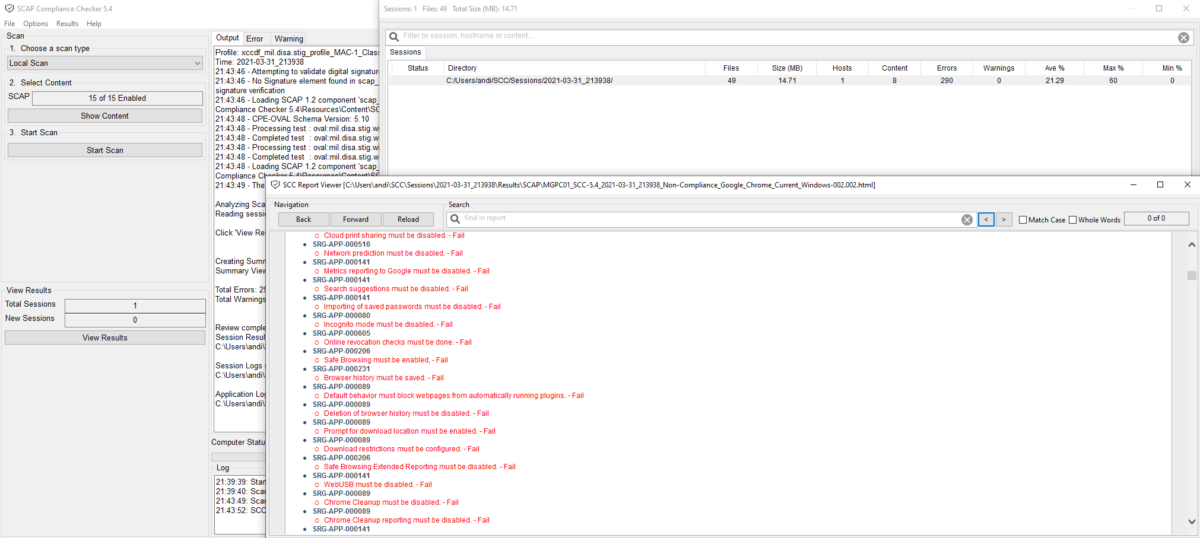
When finished, you can review the findings and recommendations directly within the tool:
Stay safe…